
PCI DSS Compliance Checklist for US E-commerce Businesses
Advertisement
Trending Now
Advertisement
Hot Articles

The Importance of Data Encryption in Cybersecurity and Privacy
 A Compliance Overview.webp)
Malaysia's Personal Data Protection Act (PDPA) A Compliance Overview
Choosing the Right Data Security Solutions for Your Business Needs

The Role of Penetration Testing in Cybersecurity Risk Management
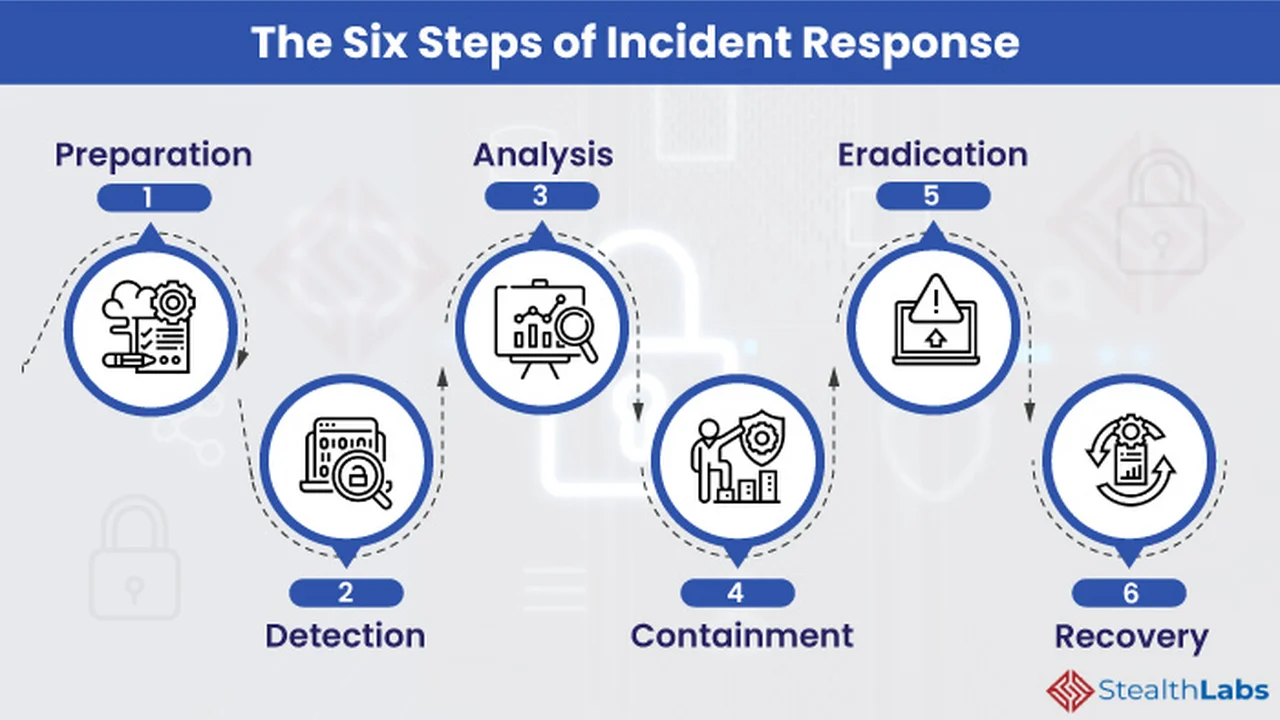
Best Practices for Developing a Cybersecurity Incident Response Plan

Cybersecurity Trends and Compliance Challenges in Southeast Asia
Advertisement

US Cybersecurity Compliance









 Strategies to Protect Sensitive Information.webp)
