Best Practices for Developing a Cybersecurity Incident Response Plan
Best Practices for Developing a Cybersecurity Incident Response Plan: Create a robust cybersecurity incident response plan. Discover best practices for preparation, detection, containment, eradication, and recovery from cyberattacks.
Why You Absolutely Need an Incident Response Plan (IRP)
Let's face it, no matter how strong your defenses are, cyberattacks *can* happen. It's not a matter of *if*, but *when*. That's where a solid Cybersecurity Incident Response Plan (IRP) comes in. Think of it as your emergency playbook for when things go south. Without one, you're basically scrambling in the dark, wasting precious time and potentially making the situation worse.
A well-defined IRP helps you:
* Minimize Damage: Quick and decisive action can limit the impact of a breach.
* Reduce Downtime: Get back to business faster.
* Protect Your Reputation: Show customers and stakeholders you take security seriously.
* Comply with Regulations: Many compliance standards (like HIPAA, GDPR, etc.) require an IRP.
* Lower Costs: A coordinated response is cheaper than a chaotic one.
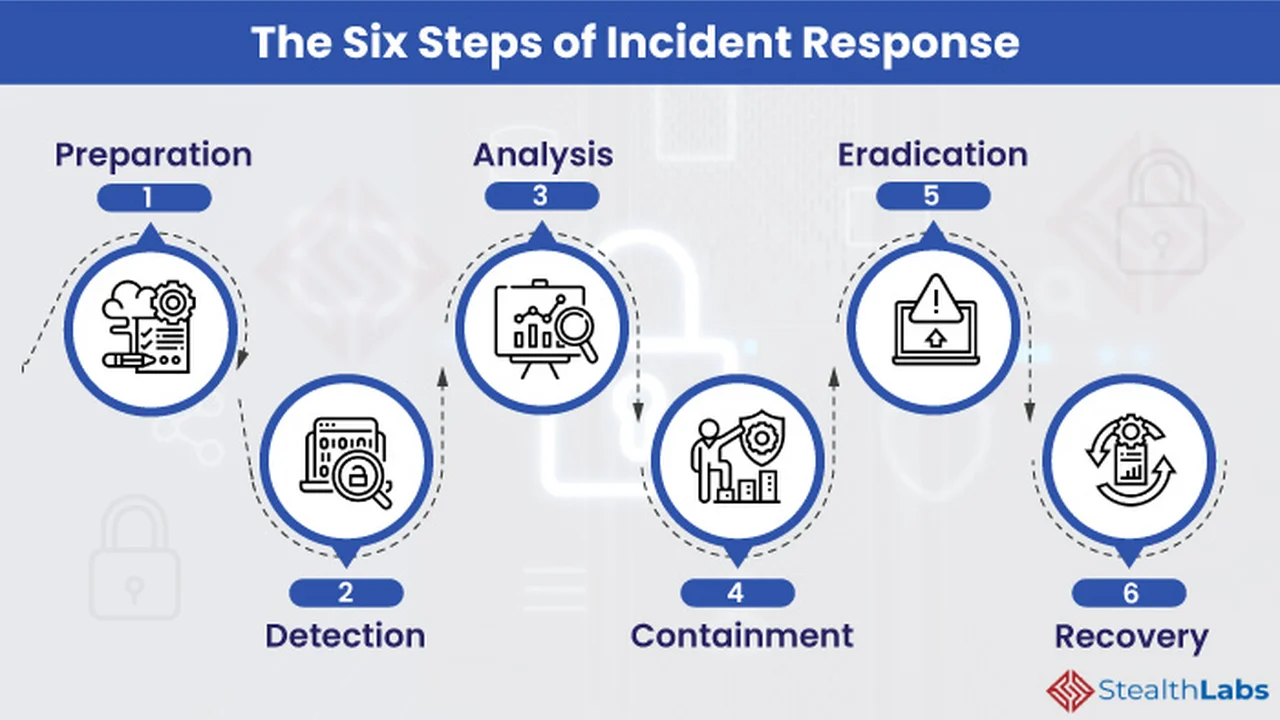
Preparation is Key: Building Your Foundation for Cybersecurity Incident Response
Before an incident even occurs, you need to lay the groundwork. Preparation is the cornerstone of an effective IRP. This involves several crucial steps:
1. Assembling Your Incident Response Team: The Cybersecurity Dream Team
Identify key personnel from different departments (IT, legal, communications, management). Clearly define roles and responsibilities. Who's in charge? Who talks to the media? Who handles technical analysis? Having a designated team ensures everyone knows their part when the pressure's on.
2. Developing Clear Communication Channels: Cybersecurity Communication is Critical
Establish secure and reliable communication channels for the team to use during an incident. Consider using encrypted messaging apps, dedicated phone lines, or even physical meeting locations. Make sure these channels are tested regularly.
3. Conducting Regular Risk Assessments: Cybersecurity Risk Assessment Matters
Identify your most critical assets and potential threats. What are your biggest vulnerabilities? What are the likely attack vectors? Knowing your weaknesses allows you to prioritize your response efforts.
4. Defining Incident Categories and Severity Levels: Classifying Cybersecurity Incidents
Categorize incidents based on their type (e.g., malware infection, data breach, phishing attack) and severity (e.g., low, medium, high). This helps you prioritize incidents and allocate resources accordingly. A minor malware infection on a single workstation is handled differently than a large-scale data breach.
5. Creating and Maintaining an Asset Inventory: Cybersecurity Asset Management
Keep a detailed inventory of all your hardware, software, and data assets. This makes it easier to identify affected systems during an incident and track the progress of your response.
Detection and Analysis: Spotting the Cybersecurity Fire Early
Early detection is crucial to minimizing the impact of a cyberattack. This involves monitoring your systems for suspicious activity and quickly analyzing potential incidents.
6. Implementing Security Monitoring Tools: Cybersecurity Monitoring Tools
Deploy tools like Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), and endpoint detection and response (EDR) solutions to monitor your network and systems for suspicious activity. These tools can automatically detect and alert you to potential incidents.
7. Establishing Clear Incident Reporting Procedures: Cybersecurity Incident Reporting
Make it easy for employees to report suspected incidents. Provide clear instructions and a dedicated reporting channel. Encourage employees to report anything that seems suspicious, even if they're not sure it's an actual incident. No penalty for reporting something that turns out to be nothing, but *huge* penalty for not reporting a real incident.
8. Performing Initial Triage and Analysis: Cybersecurity Incident Analysis
When an incident is reported, quickly assess its severity and potential impact. Gather as much information as possible to determine the scope of the incident and identify affected systems. Use threat intelligence feeds to understand the attacker's tactics and techniques.
Containment, Eradication, and Recovery: Putting Out the Cybersecurity Fire
Once an incident has been detected and analyzed, the next step is to contain the damage, eradicate the threat, and recover your systems.
9. Isolating Affected Systems: Cybersecurity Incident Containment
Immediately isolate affected systems from the network to prevent the incident from spreading. This may involve disconnecting computers from the network, shutting down servers, or blocking access to specific websites or applications. Quarantine, quarantine, quarantine!
10. Eradicating the Threat: Cybersecurity Threat Eradication
Remove the malware or other malicious code from affected systems. This may involve running antivirus scans, restoring systems from backups, or rebuilding systems from scratch. Make sure you thoroughly clean all affected systems to prevent reinfection.
11. Recovering Systems and Data: Cybersecurity Data Recovery
Restore affected systems and data from backups. Verify the integrity of the restored data to ensure it hasn't been corrupted. Monitor the recovered systems closely for any signs of further compromise.
Post-Incident Activity: Learning from the Cybersecurity Experience
The incident isn't over when the systems are back online. It's crucial to learn from the experience and improve your IRP.
12. Conducting a Post-Incident Review: Cybersecurity Post-Mortem
Conduct a thorough review of the incident to identify what went wrong and what could have been done better. Document the lessons learned and use them to improve your IRP.
13. Updating Your Incident Response Plan: Cybersecurity IRP Updates
Based on the post-incident review, update your IRP to address any identified weaknesses. Make sure the updated plan is communicated to the entire team.
14. Testing Your Incident Response Plan: Cybersecurity IRP Testing
Regularly test your IRP through tabletop exercises or simulated attacks. This helps you identify any gaps in the plan and ensure that the team is prepared to respond effectively to a real incident. Think of it as a fire drill for your cybersecurity.
Recommended Cybersecurity Incident Response Products and Tools
Here are a few examples of tools that can assist in various stages of your incident response:
* SIEM (Security Information and Event Management):
* Splunk Enterprise Security: A powerful SIEM platform that provides real-time security monitoring, threat detection, and incident investigation capabilities.
* Use Case: Monitoring network traffic, identifying suspicious activity, and correlating events from different security devices.
* Comparison: Offers more advanced analytics and customization options compared to some other SIEM solutions, but can be more complex to set up and manage.
* Pricing: Varies depending on the size of your organization and the amount of data you need to analyze. Contact Splunk for a quote.
* IBM QRadar: Another leading SIEM platform that provides comprehensive security intelligence and analytics.
* Use Case: Detecting and responding to advanced threats, such as insider threats and zero-day exploits.
* Comparison: Known for its strong threat intelligence capabilities and integration with other IBM security products.
* Pricing: Similar to Splunk, pricing is based on your organization's needs. Contact IBM for a quote.
* EDR (Endpoint Detection and Response):
* CrowdStrike Falcon: A cloud-based EDR solution that provides real-time threat detection and response capabilities for endpoints.
* Use Case: Detecting and preventing malware infections, ransomware attacks, and other endpoint threats.
* Comparison: Offers excellent threat intelligence and automated response capabilities.
* Pricing: Subscription-based pricing, varies depending on the number of endpoints you need to protect.
* SentinelOne Singularity: An AI-powered EDR solution that provides autonomous threat detection and response.
* Use Case: Detecting and responding to advanced threats that bypass traditional antivirus solutions.
* Comparison: Known for its ability to automatically detect and respond to threats without human intervention.
* Pricing: Subscription-based pricing, varies depending on the number of endpoints you need to protect.
* Incident Response Platforms:
* Palo Alto Networks Cortex XSOAR (formerly Demisto): A security orchestration, automation, and response (SOAR) platform that automates incident response workflows.
* Use Case: Automating tasks such as threat intelligence enrichment, incident triage, and response actions.
* Comparison: Helps streamline incident response processes and improve efficiency.
* Pricing: Contact Palo Alto Networks for pricing information.
* Swimlane: Another leading SOAR platform that provides a visual interface for designing and automating incident response workflows.
* Use Case: Automating tasks such as phishing analysis, malware analysis, and vulnerability management.
* Comparison: Offers a user-friendly interface and a wide range of integrations with other security tools.
* Pricing: Contact Swimlane for pricing information.
Remember to choose products that fit your specific needs and budget. Consider factors such as the size of your organization, the complexity of your IT environment, and your security requirements.
:max_bytes(150000):strip_icc()/277019-baked-pork-chops-with-cream-of-mushroom-soup-DDMFS-beauty-4x3-BG-7505-5762b731cf30447d9cbbbbbf387beafa.jpg)