Top 5 Cybersecurity Frameworks for Risk Management and Compliance
Compare the top 5 cybersecurity frameworks including NIST, ISO 27001, COBIT, and CIS Controls for effective risk management and compliance. Choose the best fit for your organization.
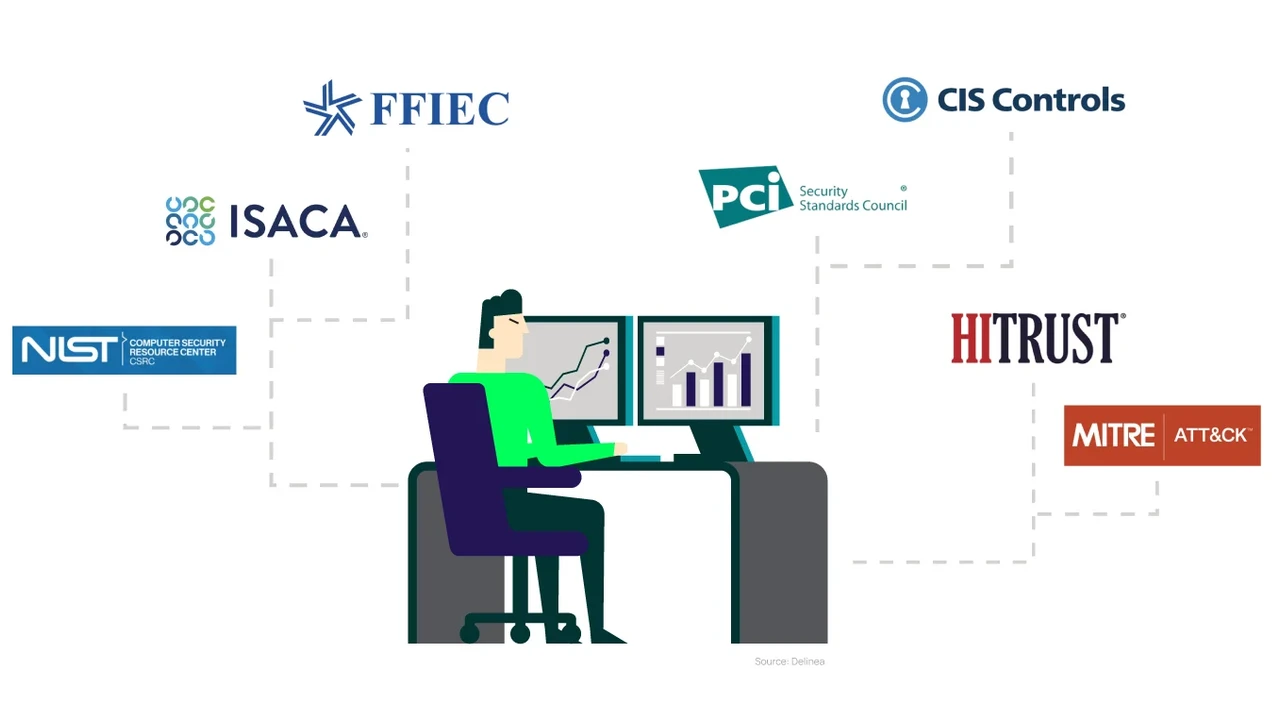
Introduction to Cybersecurity Frameworks
Hey there! Navigating the world of cybersecurity can feel like wandering through a maze, right? That's where cybersecurity frameworks come in. Think of them as your trusty map and compass, guiding you through the complexities of protecting your data and systems. These frameworks are essentially sets of guidelines, best practices, and standards designed to help organizations manage their cybersecurity risks effectively. They provide a structured approach to identifying vulnerabilities, implementing security controls, and ensuring ongoing compliance.
Why Use a Cybersecurity Framework?
So, why bother with a framework at all? Well, for starters, they provide a common language and structure for discussing cybersecurity within your organization. They also help you prioritize your security efforts, ensuring you're focusing on the most critical risks. Plus, many frameworks align with regulatory requirements, making compliance a whole lot easier. Using a framework demonstrates to your customers, partners, and stakeholders that you take security seriously. It's a sign of maturity and responsibility in today's digital landscape.
The Top 5 Cybersecurity Frameworks
Alright, let's dive into the top contenders. We're going to look at NIST, ISO 27001, COBIT, CIS Controls, and a bonus one: SOC 2.
NIST Cybersecurity Framework: A US Government Standard for IT Security
The NIST Cybersecurity Framework (CSF) is a popular choice, especially in the US. Developed by the National Institute of Standards and Technology (NIST), it's a voluntary framework based on existing standards, guidelines, and practices. The CSF is known for its flexibility and adaptability, making it suitable for organizations of all sizes and industries. It’s organized into five core functions: Identify, Protect, Detect, Respond, and Recover. Each function is further divided into categories and subcategories providing a detailed roadmap for improving your cybersecurity posture.
Use Case: A small manufacturing company can use the NIST CSF to identify critical assets, implement access controls, and establish incident response procedures to protect against ransomware attacks.
ISO 27001: An International Standard for Information Security Management
ISO 27001 is an internationally recognized standard for information security management systems (ISMS). Unlike NIST, which is more of a framework, ISO 27001 is a standard that you can get certified against. It provides a comprehensive set of controls covering everything from physical security to human resources security. Achieving ISO 27001 certification demonstrates a strong commitment to information security and can be a valuable asset for organizations seeking to win new business or comply with international regulations.
Use Case: A SaaS provider seeking to expand into the European market can achieve ISO 27001 certification to demonstrate compliance with GDPR and build trust with potential customers.
COBIT: IT Governance and Management Framework for Cybersecurity Compliance
COBIT (Control Objectives for Information and Related Technologies) is a framework focused on IT governance and management. It helps organizations align their IT strategy with their business goals and manage IT-related risks. COBIT provides a structured approach to planning, building, running, and monitoring IT processes, ensuring that IT resources are used effectively and efficiently. While not solely focused on cybersecurity, COBIT provides a valuable framework for managing IT risks, including cybersecurity risks.
Use Case: A financial institution can use COBIT to align its IT strategy with its business objectives and ensure that its IT processes are effectively managing cybersecurity risks and complying with regulatory requirements.
CIS Controls: A Prioritized Set of Actions for Cybersecurity Implementation
The CIS Controls (formerly known as the SANS Top 20) are a prioritized set of actions that organizations can take to improve their cybersecurity posture. These controls are based on real-world attack data and are designed to address the most common and critical cyber threats. The CIS Controls are known for their practicality and ease of implementation, making them a good starting point for organizations that are new to cybersecurity. They're also regularly updated to reflect the latest threat landscape.
Use Case: A non-profit organization with limited resources can implement the CIS Controls to quickly and effectively improve its cybersecurity posture and protect against common cyber threats.
SOC 2: Auditing Procedure for Service Organization Control for Data Security
SOC 2 (Service Organization Control 2) isn't exactly a framework, but it's a crucial auditing procedure, especially for service organizations that store customer data in the cloud. SOC 2 compliance demonstrates that you have implemented controls to protect the security, availability, processing integrity, confidentiality, and privacy of customer data. A SOC 2 report is often required by customers before they will entrust their data to a service provider.
Use Case: A cloud-based CRM provider needs to undergo a SOC 2 audit to demonstrate to its customers that it has implemented adequate controls to protect their data.
Comparing the Cybersecurity Frameworks: NIST vs ISO 27001 vs COBIT vs CIS Controls
So, which framework is right for you? Here's a quick comparison:
- NIST CSF: Flexible, adaptable, good starting point, widely recognized in the US.
- ISO 27001: Internationally recognized, certifiable, comprehensive, demonstrates strong commitment to security.
- COBIT: Focuses on IT governance and management, aligns IT strategy with business goals.
- CIS Controls: Practical, easy to implement, prioritized actions, good for organizations with limited resources.
Consider your organization's size, industry, regulatory requirements, and security goals when making your decision. You might even choose to adopt a hybrid approach, combining elements from different frameworks to create a customized solution that meets your specific needs.
Cybersecurity Products and Solutions for Implementing Frameworks
Okay, let's talk tools! Implementing a cybersecurity framework isn't just about documentation; it's about putting security controls in place. Here are a few product categories and specific examples to help you along the way:
Security Information and Event Management (SIEM)
SIEM solutions collect and analyze security logs from across your network, helping you detect and respond to threats in real-time.
- Splunk Enterprise Security: A powerful SIEM platform with advanced analytics and threat intelligence capabilities. (Price: Varies based on data ingestion volume; typically starts around $5,500/year)
- IBM QRadar: A comprehensive SIEM solution that integrates with other IBM security products. (Price: Varies based on EPS (Events Per Second) and data storage; typically starts around $8,000/year)
- Sumo Logic: A cloud-native SIEM platform that offers scalability and ease of use. (Price: Subscription-based; starts around $1,500/month)
Vulnerability Scanners
Vulnerability scanners identify security weaknesses in your systems and applications, allowing you to remediate them before attackers can exploit them.
- Nessus Professional: A widely used vulnerability scanner with a large database of known vulnerabilities. (Price: Around $3,000/year)
- Rapid7 InsightVM: A vulnerability management solution that provides risk-based prioritization and remediation guidance. (Price: Varies based on asset count; typically starts around $5,000/year)
- Qualys VMDR: A cloud-based vulnerability management solution that integrates with other Qualys security products. (Price: Subscription-based; starts around $2,000/month)
Endpoint Detection and Response (EDR)
EDR solutions monitor endpoints for malicious activity and provide tools for investigating and responding to threats.
- CrowdStrike Falcon Insight: A leading EDR platform with advanced threat detection and prevention capabilities. (Price: Varies based on endpoint count; typically starts around $100/endpoint/year)
- SentinelOne Singularity XDR: An AI-powered EDR solution that provides autonomous threat protection. (Price: Varies based on endpoint count; typically starts around $80/endpoint/year)
- Microsoft Defender for Endpoint: An EDR solution integrated with Windows 10 and other Microsoft security products. (Price: Included with Microsoft 365 E5 licenses or available as a standalone subscription; starts around $5/user/month)
Access Control and Identity Management Tools
These tools help you manage user access to systems and data, ensuring that only authorized individuals have access to sensitive information.
- Okta Identity Cloud: Cloud based identity and access management. (Price: Starts around $2/user/month)
- Microsoft Azure AD: Cloud based, integrates well with Microsoft products. (Price: Included with some Microsoft 365 licenses, starts around $6/user/month)
- CyberArk: Focuses on privileged access management. (Price: Varies greatly based on modules and scale. Contact for quote)
Making the Right Choice for Your Organization
Choosing the right cybersecurity framework and tools is a critical decision that requires careful consideration. Don't be afraid to seek expert advice and conduct thorough evaluations to find the best fit for your organization. Remember, cybersecurity is an ongoing process, not a one-time fix. Stay informed, adapt to the evolving threat landscape, and continuously improve your security posture.
:max_bytes(150000):strip_icc()/277019-baked-pork-chops-with-cream-of-mushroom-soup-DDMFS-beauty-4x3-BG-7505-5762b731cf30447d9cbbbbbf387beafa.jpg)